Discovering the Ultimate Armor in Fallout 76
What is the best armor in 76? As players immerse themselves in the post-apocalyptic world of Fallout 76, they are constantly on the lookout for …
Read Article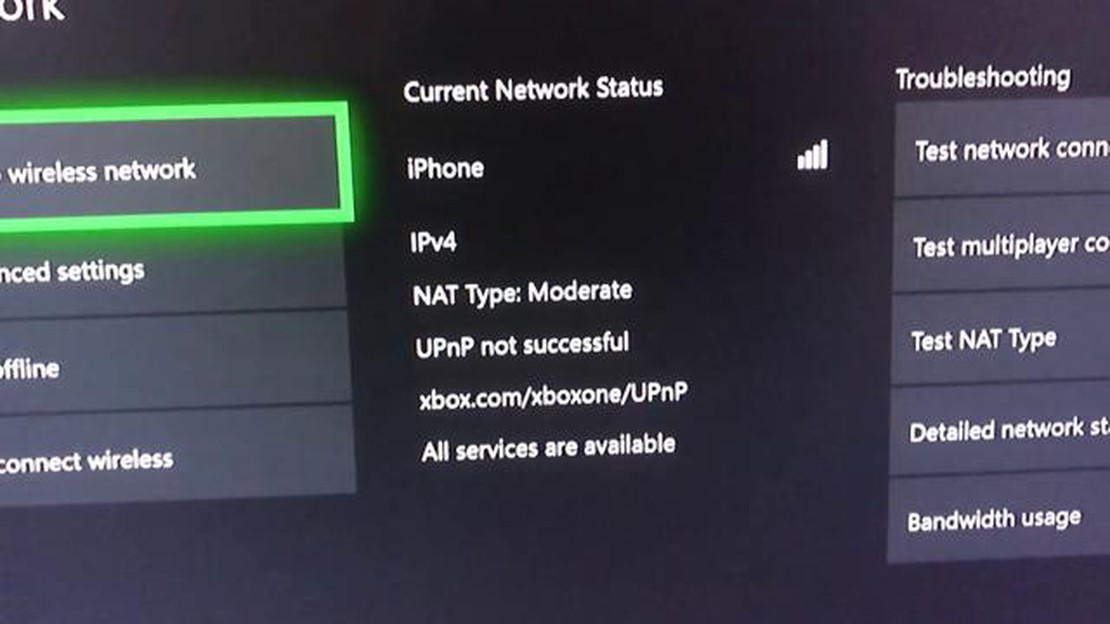
The Universal Plug and Play (UPnP) protocol has become an integral part of many modern devices, allowing them to discover and communicate with each other seamlessly. Whether it’s gaming consoles, smart TVs, or even home automation systems, UPnP simplifies the process of setting up and managing these devices. However, when UPnP fails to work as intended, it can have serious implications for users.
One area where unsuccessful UPnP can have a significant impact is in gaming. Online gaming relies heavily on UPnP to establish connections between players and enable seamless multiplayer experiences. When UPnP fails, players may encounter issues such as difficulties joining games, disconnects, or high latency, all of which can have a detrimental effect on gameplay and overall user experience.
Moreover, unsuccessful UPnP can also affect general device functionality. For example, smart TVs that rely on UPnP may struggle to discover and connect to other devices on the same network, limiting their ability to stream content or access media files. Similarly, home automation systems that depend on UPnP may fail to control connected devices, causing inconvenience and frustration.
In addition to gaming and general device functionality, the implications of unsuccessful UPnP also extend to security. UPnP is often targeted by hackers as it opens up potential vulnerabilities in the network. When UPnP fails, it can leave devices exposed to unauthorized access and compromise, jeopardizing personal data and privacy. Therefore, understanding the implications of unsuccessful UPnP is crucial for users to mitigate the risks and take necessary precautions to safeguard their devices and network.
UPnP, or Universal Plug and Play, is a network protocol that allows devices to discover and connect with each other in a network. It provides automatic port forwarding, which is essential for online gaming, media streaming, and other applications that require Internet connectivity.
However, when UPnP fails to work properly, it can have several implications. One major implication is the inability to establish connections with other devices, which can result in the inability to play online games with friends or access media files on a network.
Another implication is the vulnerability of the network to unauthorized access. UPnP can open ports on a router automatically, and if this feature is not working as intended, it can leave the network exposed to potential security threats. Hackers may exploit these open ports to gain unauthorized access to devices in the network or launch attacks on the network itself.
Furthermore, unsuccessful UPnP can also lead to network congestion and poor performance. When devices try to establish connections with each other, they may encounter difficulties due to UPnP failures. This can result in increased latency, packet loss, and overall degraded performance, especially in online gaming scenarios.
It is important for users to understand the implications of unsuccessful UPnP and take necessary steps to troubleshoot and resolve any issues. This may involve checking router settings, updating firmware, or even disabling UPnP and manually configuring port forwarding to ensure proper network connectivity and security.
Universal Plug and Play (UPnP) technology plays a crucial role in enhancing the gaming experience by streamlining network connectivity and enabling seamless communication between gaming devices.
With UPnP, gamers can easily connect their gaming consoles, PCs, and other devices to their home network without the need for manual configuration. This eliminates the complexities often associated with port forwarding, NAT traversal, and firewall settings, allowing gamers to quickly set up multiplayer games and connect with others online.
UPnP also simplifies the process of hosting gaming sessions by automatically configuring the necessary network settings, such as opening the required ports for multiplayer games. This ensures that other players can easily join the hosted game without any additional configuration steps.
Additionally, UPnP enables gamers to take advantage of features like voice chat, video streaming, and content sharing during gameplay. By automatically establishing the necessary connections between devices, UPnP allows gamers to communicate and collaborate with other players in real-time, enhancing the overall gaming experience.
Furthermore, UPnP facilitates the discovery of available gaming services and devices on the network. Through UPnP-enabled devices, gamers can easily find and connect to gaming servers, browse for multiplayer games, and discover new gaming experiences.
In summary, the role of UPnP in gaming is to simplify network connectivity and enhance the overall gaming experience. By eliminating the complexities of manual network configuration, UPnP enables gamers to quickly set up multiplayer games, communicate in real-time, and discover new gaming opportunities.
When a UPnP configuration fails, it can have several negative consequences for the user and their network. One of the main consequences is the inability to establish a proper network connection for certain devices, such as gaming consoles or media streaming devices.
This can lead to frustrating experiences for users, as they may not be able to access online gaming features, connect to game servers, or stream their favorite content. Without a successful UPnP configuration, these devices may not be able to communicate effectively with the network, resulting in limited functionality.
Furthermore, failed UPnP configurations can also pose security risks for the network. UPnP allows devices to automatically open ports in the router’s firewall, which can be convenient for certain applications but can also leave the network vulnerable to malicious attacks.
When the UPnP configuration fails, these ports may not be properly opened or closed, leaving them exposed to potential threats. It is essential for users to understand the implications of failed UPnP configurations and take necessary measures to ensure network security.
In addition to these immediate consequences, failed UPnP configurations can also have long-term implications. If users are unable to resolve the configuration issues, they may need to resort to manual port forwarding, which can be time-consuming and complicated.
Moreover, UPnP failures could indicate underlying issues with the network or the router itself. It may be a sign of outdated firmware, hardware limitations, or other technical problems that need to be addressed in order to optimize the network performance.
To summarize, failed UPnP configurations can result in limited functionality and connectivity for devices, potential security risks, and long-term network performance issues. It is crucial for users to troubleshoot and resolve these configuration failures promptly to ensure a seamless and secure network experience.
Network vulnerabilities and risks can pose significant threats to the security and functionality of a network system. Understanding and identifying these vulnerabilities is essential for organizations to effectively protect their data and infrastructure. By proactively identifying potential risks, organizations can implement appropriate security measures to mitigate these risks and ensure a robust network environment.
Read Also: Common Reasons and Solutions for PS4 Slim Power Cycling
One common network vulnerability is weak authentication measures. If a network system relies on simple or commonly used passwords, it becomes vulnerable to brute force attacks. Implementing strong password policies and multi-factor authentication can help mitigate this risk. Additionally, regularly auditing user accounts and removing inactive ones can help prevent unauthorized access.
Another vulnerability is outdated software and firmware. Exploiting known vulnerabilities in outdated software is a common strategy used by hackers. Regularly updating and patching software and firmware ensures that any known vulnerabilities are addressed and minimizes the risk of unauthorized access or data breaches.
Read Also: Is Murata Himeko in Genshin Impact?
Malware infections present another significant risk to network security. Malware can be introduced through email attachments, compromised websites, or infected devices. Regularly scanning for malware, implementing firewalls and intrusion detection systems, and educating users on safe browsing habits are essential for minimizing the risk of malware infections.
Social engineering attacks are yet another common vulnerability that organizations must be aware of. These attacks exploit human psychology to deceive users into revealing confidential information or granting unauthorized access. Employees should receive regular training on how to recognize and respond to social engineering tactics to reduce the risk of falling victim to these attacks.
Network vulnerabilities can also arise from misconfigured devices or insecure network architecture. Regular network assessments, including vulnerability scans, can help identify misconfigurations and weaknesses in the network infrastructure. Proper network segmentation, implementing access controls, and using encryption protocols can help mitigate these risks.
Overall, identifying network vulnerabilities and risks is crucial for maintaining a secure network environment. By proactively addressing these vulnerabilities, organizations can significantly reduce the likelihood of security breaches and ensure the integrity of their data and infrastructure.
UPnP (Universal Plug and Play) is a network protocol that allows devices to automatically discover and communicate with each other on a local network. While UPnP offers convenience and ease of use, its unsuccessful implementation can pose significant risks to data security.
One of the main concerns with unsuccessful UPnP is that it can enable unauthorized access to sensitive information. If a device’s UPnP implementation is flawed or outdated, hackers can exploit vulnerabilities to gain access to the device and potentially extract or manipulate data.
Additionally, unsuccessful UPnP can lead to unintended exposure of private information. For example, if a device’s UPnP configuration is not properly secured, it may inadvertently expose private files or services to the public internet, making them accessible to anyone with malicious intent.
Another consequence of unsuccessful UPnP is the potential for unauthorized control or manipulation of devices. If a device’s UPnP functionality is compromised, an attacker can gain control over the device and perform malicious actions, such as changing settings, stealing sensitive data, or even launching attacks on other devices on the network.
To mitigate the risks associated with unsuccessful UPnP, it is crucial to keep devices and software up to date with the latest security patches. Additionally, it is important to regularly review and configure UPnP settings to ensure they are properly secured and only allow necessary communication between devices.
In conclusion, the implications of unsuccessful UPnP on data security can be severe. It is essential for users and device manufacturers to prioritize security and take appropriate measures to prevent unauthorized access, exposure of private information, and unauthorized control of devices.
The security of UPnP (Universal Plug and Play) has become a growing concern in recent years, with numerous vulnerabilities and attacks being discovered. As technology continues to advance, it is crucial to stay informed about the latest news and updates on UPnP security issues.
One of the most significant updates in UPnP security is the identification and patching of exploitable vulnerabilities. Security experts have been working diligently to identify these vulnerabilities and release patches to mitigate the risk they pose. Regularly checking for and applying these updates is essential for maintaining the security of devices that rely on UPnP.
Another important update is the awareness surrounding the risks associated with UPnP. People are becoming increasingly aware of the potential security risks that come with enabling UPnP on their devices. This awareness has prompted more discussions and efforts to educate users about the importance of disabling UPnP if not necessary and implementing additional security measures.
The ongoing news surrounding UPnP security issues also highlights the importance of utilizing strong passwords. Weak or default passwords can make it easier for attackers to gain unauthorized access to devices with UPnP enabled. Users should be encouraged to create unique, complex passwords for their devices and regularly update them to reduce the risk of unauthorized access.
In conclusion, staying informed about the latest news and updates on UPnP security issues is crucial in order to protect devices and networks from potential vulnerabilities and attacks. By regularly checking for updates, raising awareness about risks, using strong passwords, implementing network segmentation, and prioritizing security in development, users and organizations can mitigate the risks associated with UPnP.
UPnP (Universal Plug and Play) is a set of networking protocols that allows devices to discover and communicate with each other on a local area network. It enables devices such as computers, printers, and routers to automatically configure themselves and establish network connections without the need for manual setup.
UPnP works by using a combination of protocols, including SSDP (Simple Service Discovery Protocol) for device discovery, SOAP (Simple Object Access Protocol) for device control, and HTTP (Hypertext Transfer Protocol) for communication between devices. When a new device is added to the network, it broadcasts a message to discover other devices and services available on the network.
UPnP offers several benefits, such as ease of use, automatic device configuration, and seamless communication between devices. It simplifies the setup process for network devices, allows for easy sharing of media and resources, and enables devices to work together more efficiently. UPnP also provides a standardized way for devices from different manufacturers to interoperate.
Unsuccessful UPnP implementations can lead to security vulnerabilities and potential compromises of network devices. If UPnP is not properly implemented or configured, it can expose devices to external threats and attacks. Poorly secured UPnP can also result in unauthorized access to network resources and sensitive information, as well as the potential for malicious activities.
Unsuccessful UPnP implementations can compromise the security of a network by exposing devices to unauthorized access, enabling remote control or surveillance of devices without the user’s knowledge, and allowing malicious actors to exploit vulnerabilities in UPnP implementations to gain control over network resources. This can result in data breaches, privacy violations, and potential damage to the network infrastructure.
To mitigate the risks associated with UPnP, it is recommended to disable UPnP if it is not necessary for the operation of the network. If UPnP is required, it is important to keep the UPnP implementation up to date with the latest security patches and firmware updates. Additionally, configuring UPnP properly, such as enabling strong authentication and access controls, can help reduce the risk of unauthorized access and malicious activities.
Yes, there are alternative technologies and protocols to UPnP, such as DLNA (Digital Living Network Alliance) and Bonjour (Apple’s zero-configuration networking). These technologies offer similar functionalities to UPnP but may have different implementation approaches and device compatibility. It is important to evaluate the specific requirements and compatibility of the network devices before choosing an alternative to UPnP.
What is the best armor in 76? As players immerse themselves in the post-apocalyptic world of Fallout 76, they are constantly on the lookout for …
Read ArticleHow do I take a screenshot of Landorus without having him? If you are an avid Pokémon player, you may be wondering how to capture the majestic …
Read ArticleWhat is QHD vs UHD? In the world of gaming and technology, display resolutions play a crucial role in providing an immersive and visually stunning …
Read ArticleWho is the girlfriend of Henry Danger and what is their relationship like? Henry Danger is a popular American superhero comedy television series that …
Read ArticleWhat is Mita MOVO Lata in Hilichurl? Exploring the vast and enchanting world of Genshin Impact, players have come across many intriguing characters …
Read ArticleWhy does HDR look worse? High Dynamic Range (HDR) technology has taken the gaming and media industry by storm, promising to revolutionize the way we …
Read Article